| | | 'CryptoLocker Ransomware' is aparrently on the loose ...
It evidently made an attempt on me yesterday and was trapped by Norton IS, after evidently being trapped in a Malwarebytes TEMP file. Malwarebytes (run with shields up) may have trapped it first.
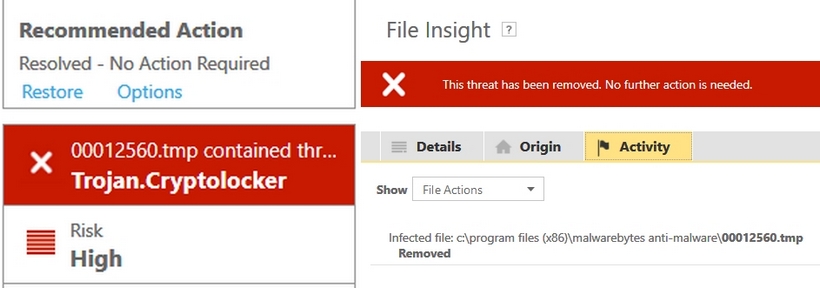
CryptoLocker is a ransomware trojan which targeted computers running Microsoft Windows,[1] believed to have first been posted to the Internet on 5 September 2013.[2] CryptoLocker propagated via infected email attachments, and via an existing botnet; when activated, the malware encrypts certain types of files stored on local and mounted network drives using RSA public-key cryptography, with the private key stored only on the malware's control servers. The malware then displays a message which offers to decrypt the data if a payment (through either bitcoin or a pre-paid cash voucher) is made by a stated deadline, and threatened to delete the private key if the deadline passes. If the deadline is not met, the malware offered to decrypt data via an online service provided by the malware's operators, for a significantly higher price in bitcoin.
CryptoLocker is typically propagated as an attachment to a seemingly innocuous e-mail message, which appears to have been sent by a legitimate company as a ZIP file attached to an email message which contains an executable file with the filename and the icon disguised as a PDF file, taking advantage of Windows' default behaviour of hiding the extension from file names to disguise the real .EXE extension. CryptoLocker was also propagated using the Gameover ZeuS trojan and botnet.
- Eric E-L - |
|





