A First Look at the Target Intrusion, Malware
...............................................................................
1/14/2014
krebsonsecurity.com
..............................Last weekend, Target finally disclosed at least one cause of the massive data breach that exposed personal and financial information on more than 110 million customers: Malicious software that infected point-of-sale systems at Target checkout counters. Today’s post includes new information about the malware apparently used in the attack, according to two sources with knowledge of the matter.
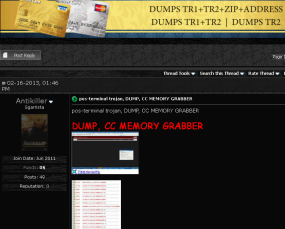 The seller of the point-of-sale “memory dump” malware allegedly used in the Target attack. The seller of the point-of-sale “memory dump” malware allegedly used in the Target attack.
In an interview with CNBC on Jan. 12, Target CEO Gregg Steinhafel confirmed that the attackers stole card data by installing malicious software on point-of-sale (POS) devices in the checkout lines at Target stores. A report published by Reuters that same day stated that the Target breach involved memory-scraping malware.
This type of malicious software uses a technique that parses data stored briefly in the memory banks of specific POS devices; in doing so, the malware captures the data stored on the card’s magnetic stripe in the instant after it has been swiped at the terminal and is still in the system’s memory. Armed with this information, thieves can create cloned copies of the cards and use them to shop in stores for high-priced merchandise. Earlier this month, U.S. Cert issued a detailed analysis of several common memory scraping malware variants.
Target hasn’t officially released details about the POS malware involved, nor has it said exactly how the bad guys broke into their network. Since the breach, however, at least two sources with knowledge of the ongoing investigation have independently shared information about the point-of-sale malware and some of the methods allegedly used in the attack.
‘BLACK POS’
On Dec. 18, three days after Target became aware of the breach and the same day this blog broke the story, someone uploaded a copy of the point-of-sale malware used in the Target breach to ThreatExpert.com, a malware scanning service owned by security firm Symantec. The report generated by that scan was very recently removed, but it remains available via Google cache (Update, Jan. 16, 9:29 a.m.: Sometime after this story ran, Google removed the cached ThreatExpert report; I’ve uploaded a PDF version of it here).
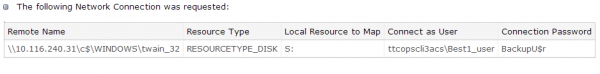 According to sources, “ttcopscli3acs” is the name of the Windows computer name/domain used by the POS malware planted at Target stores; the username that the thieves used to log in remotely and download stolen card data was “Best1_user”; the password was “BackupU$r” According to sources, “ttcopscli3acs” is the name of the Windows computer name/domain used by the POS malware planted at Target stores; the username that the thieves used to log in remotely and download stolen card data was “Best1_user”; the password was “BackupU$r”
According to a source close to the investigation, that threatexpert.com report is related to the malware analyzed at this Symantec writeup (also published Dec. 18) for a point-of-sale malware strain that Symantec calls “Reedum” (note the Windows service name of the malicious process is the same as the ThreatExpert analysis –”POSWDS”). Interestingly, a search in Virustotal.com — a Google-owned malware scanning service — for the term “reedum” suggests that this malware has been used in previous intrusions dating back to at least June 2013; in the screen shot below left, we can see a notation added to that virustotal submission, “30503 POS malware from FBI”.
The source close to the Target investigation said that at the time this POS malware was installed in Target’s environment (sometime prior to Nov. 27, 2013), none of the 40-plus commercial antivirus tools used to scan malware at virustotal.com flagged the POS malware (or any related hacking tools that were used in the intrusion) as malicious. “They were customized to avoid detection and for use in specific environments,” the source said.
 That source and one other involved in the investigation who also asked not to be named said the POS malware appears to be nearly identical to a piece of code sold on cybercrime forums called BlackPOS, a relatively crude but effective crimeware product. BlackPOS is a specialized piece of malware designed to be installed on POS devices and record all data from credit and debit cards swiped through the infected system. That source and one other involved in the investigation who also asked not to be named said the POS malware appears to be nearly identical to a piece of code sold on cybercrime forums called BlackPOS, a relatively crude but effective crimeware product. BlackPOS is a specialized piece of malware designed to be installed on POS devices and record all data from credit and debit cards swiped through the infected system.
According the author of BlackPOS — an individual who uses a variety of nicknames, including “Antikiller” — the POS malware is roughly 207 kilobytes in size and is designed to bypass firewall software. The barebones “budget version” of the crimeware costs $1,800, while a more feature-rich “full version” — including options for encrypting stolen data, for example — runs $2,300.
THE ATTACK
Target has yet to honor a single request for comment from this publication, and the company has said nothing publicly about how this breach occurred. But according to sources, the attackers broke in to Target after compromising a company Web server. Somehow, the attackers were able to upload the malicious POS software to store point-of-sale machines, and then set up a control server within Target’s internal network that served as a central repository for data hoovered by all of the infected point-of-sale devices.
“The bad guys were logging in remotely to that [control server], and apparently had persistent access to it,” a source close to the investigation told KrebsOnSecurity. “They basically had to keep going in and manually collecting the dumps.”
It’s not clear what type of software powers the point-of-sale devices running at registers in Target’s U.S. stores, but multiple sources say U.S. stores have traditionally used a home-grown software called Domain Center of Excellence, which is housed on Windows XP Embedded and Windows Embedded for Point of Service (WEPOS). Target’s Canadian stores run POS devices from Retalix, a company recently purchased by payment hardware giant NCR. According to sources, the Retalix POS systems will be rolled out to U.S. Target locations gradually at some point in the future.
WHO IS ANTIKILLER?
 Image: Securityaffairs.co Image: Securityaffairs.co
A more full-featured Breadcrumbs-level analysis of this malware author will have to wait for another day, but for now there are some clues already dug up and assembled by Russian security firm Group-IB.
Not long after Antikiller began offering his BlackPOS crimeware for sale, Group-IB published an analysis of it, stating that “customers of major US banks, such as such as Chase (Newark, Delaware), Capital One (Virginia, Richmond), Citibank (South Dakota), Union Bank of California (California, San Diego), Nordstrom FSB Debit (Scottsdale, Arizona), were compromised by this malware.”
In his sales thread on at least one crime forum, Antikiller has posted a video of his product in action. As noted by Group-IB, there is a split second in the video where one can see a URL underneath the window being recorded by the author’s screen capture software which reveals a profile at the Russian social networking site Vkontakte.ru. Group-IB goes on to link that account to a set of young Russian and Ukranian men who appear to be actively engaged in a variety of cybercrime activities, including distributed denial-of-service (DDoS) attacks and protests associated with the hackivist collective known as Anonymous.
One final note: Dozens of readers have asked whether I have more information on other retailers that were allegedly victimized along with Target in this scheme. According to Reuters, “smaller breaches on at least three other well-known U.S. retailers took place and were conducted using similar techniques as the one on Target.” Rest assured that when and if I have information about related breaches I feel confident enough about to publish, you will read about it here first. |




